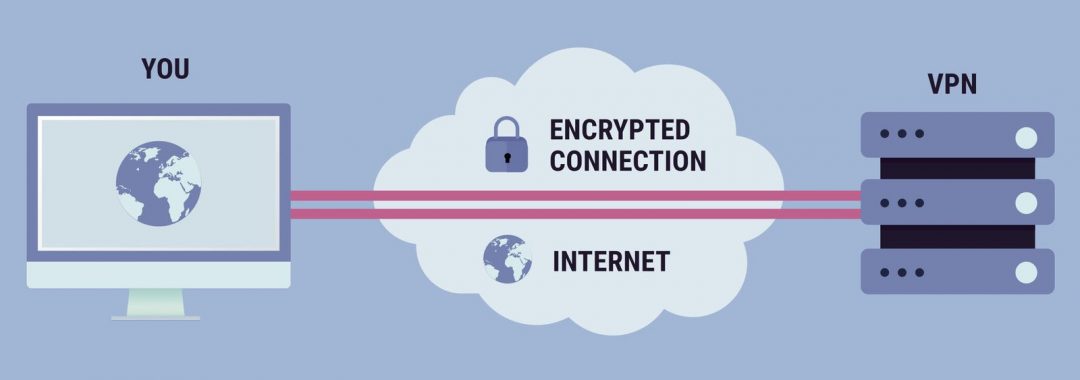
Virtual Private Networks (VPN)
VPN is an acronym for Virtual Private Network. A VPN provides an encrypted and secure connection “tunnel” path from a user’s machine to its destination through the public Internet. The Virtual Private Network (VPN) has risen fast to becomea major networking technology in just a few years. With a VPN, you can send data, via a shared or public network in a manner that emulates a point-to-point private link, between two networks
(routers), between two servers, or between a client and a server.
The remote PC (installed with a VPN client software) utilizes existing telecommunications infrastructures (e.g., phone lines, broadband services, dedicated Internet link, etc), and a tunneling protocol (incorporated with other authentication and encryption protocols) to securely access resource inside the corporate Intranet through a VPN server which sits at the perimeter of the corporate network.
Why would we need VPN ?
The world has changed a lot in the last couple of decades. Instead of simply dealing with local or regional concerns, many businesses now have to think about global markets and logistics.
Many companies have facilities spread out across the country or around the world, and there is one thing that all of them need: A way to maintain fast, secure and reliable communications wherever their offices are.
Until fairly recently, this has meant the use of leased lines to maintain a wide area network (WAN).
Leased lines, ranging from ISDN (integrated services digital network, 128 Kbps) to OC3 (Optical Carrier-3, 155 Mbps) fiber, provided a company with a way to expand its private network beyond its immediate geographic area.
A WAN had obvious advantages over a public network like the Internet when it came to reliability, performance and security.
But maintaining a WAN, particularly when using leased lines, can become quite expensive and often rises in cost as the distance between the offices increases.
As the popularity of the Internet grew, businesses turned to it as a means of extending their own networks.
First came intranets, which are password-protected sites designed for use only by company employees.
Now, many companies are creating their own VPN (virtual private network) to accommodate the needs of remote employees and distant offices.
How VPN works
Most VPNs rely on tunneling to create a private network that reaches across the Internet. Essentially, tunneling is the process of placing an entire packet within another packet and sending it over a network.
The protocol of the outer packet is understood by the network and both points, called tunnel interfaces, where the packet enters and exits the network.
Tunneling requires three different protocols:
* Carrier protocol – The protocol used by the network that the information is traveling over
* Encapsulating protocol – The protocol (GRE, IPSec, L2F, PPTP, L2TP) that is wrapped around the original data
* Passenger protocol – The original data (IPX, NetBeui, IP) being carried
Tunneling has amazing implications for VPNs. For example, you can place a packet that uses a protocol not supported on the Internet (such as NetBeui) inside an IP packet and send it safely over the Internet.
Or you could put a packet that uses a private (non-routable) IP address inside a packet that uses a globally unique IP address to extend a private network over the Internet.
Benefits of VPN
Extend geographic connectivity
Improve security
Reduce operational costs versus traditional WAN
Reduce transit time and transportation costs for remote users
Improve productivity
Simplify network topology
Provide global networking opportunities
Provide telecommuter support
Provide broadband networking compatibility
Provide faster ROI (return on investment) than traditional WAN